The Internet of Things is rapidly influencing every sphere of our lives. IoT in Automotive Industry is seeing one such rapid growth. As of 2020, an article by Deloitte cites that over 20 billion IoT devices are in use.
Overtly, the connected vehicle is the most recent embodiment of IoT technology. While automotive engineers and software developers both claim responsibility for this success, the real power behind the wheels lies with the IoT service providers.
Our cars can link to our smartphones and stream our favorite playlists for hours. But today it is equipped to provide us with emergency roadside assistance and real-time traffic alerts. With a simple click, IoT devices can evaluate engine performance, monitor and control air temperature, and measure physical indicators. Hence, automotive companies can no longer afford to overlook the contribution and role of IoT.
Internet Of Things Will Be The Backbone Of The Future Automotive Industry
The Internet of Things is ushering transformative across sectors; the automotive industry will continue to change rapidly under its influence. It will be the backbone of crucial industry changes. And the connected car will be a critical player in determining the future economy, besides providing an enjoyable user experience on the roads.
We see examples of power struggles between the software and the automotive industries. Evidently, the industry is evolving and reinventing itself. We are moving from the age of products to the age of experiences, from hardware to software, from information to value creation. The customer mindset is transitioning from siloed products to inclusive ecosystems.
As the automotive industry undergoes this overhaul in its position, IoT in automotive industry can fortify using the following methods:
- Align the vision with the automotive industry – IoT, software service providers, and the automotive industry will need to be better aligned to understand the market needs.
- Accountability of data is of paramount importance – Who owns the data, how one uses it, and how one ensures its privacy will need to be determined.
- Adopt a customer and service-centric approach for the entire automotive lifecycle.
- Accept and adopt newer capabilities in-vehicle software development.
- Address production, manufacturing, and lifecycle challenges with the help of technology, ensuring a hassle-free and integrated development.
- Form strategic partnerships to create a value chain for smart-device manufacturers.
The Changes Brought Forward By Iot In Automotive Industry:
Wireless technology lies at the heart of the Internet of Things. IoT devices collect, share, store and exchange data with other devices, making it a connected ecosystem. It is then powered by the ability to communicate without any human involvement.
IoT in automotive manufacturing is the most significant adoption – to reduce human involvement, increased time management, and improve productivity. While the cross-industry and multi-sectoral dependence on it grows, consumer use of IoT outpaces that of business.
Connected vehicles are likely to increase by 67% over the next two years with consumers’ spending on in-vehicle connectivity anticipated to double by 2030. Thus, drivers worldwide are constantly expecting their vehicles to resemble intuitive smartphones on wheels. And IoT indeed has already proven its ability to fulfill demands around this futuristic technology.
So how can the IoT developers keep pace with the demands of the automotive industry?
Predictive repairing
IoT connectivity comes with many advantages, predictive maintenance technology being one of them. A Smart car will collect performance data of the different parts and transfer it to the cloud. Then insights based on the data can help with a risk evaluation and prevention of a potential malfunction to avoid future incidents. Both private car owners and dealers of larger fleets can adopt predictive maintenance. In the future, IoT in automotive industry will play a prominent role in preventing unplanned stops or breakdowns. Also affecting the insurance and risk industry – with customized vehicle insurance premiums powered by vehicle and driver performance.
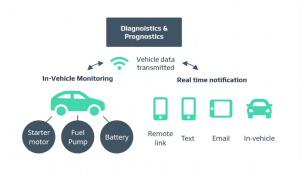
Automatic updates
IoT-powered automatic updates in connected vehicles can improve traffic management by increasing the accuracy of real-time traffic data services, enabling millions of drivers with a more comfortable and supported driving experience. As a result, many manufacturers in the automotive industry are redesigning vehicle software and hardware to comply with NDS (Navigation Data Standard) and improve vehicles’ connectivity.
Fleet Management
Truck transportation is often disregarded when adopting innovations for the automotive industry. However, there have been some breakthrough innovations. One of the most significant examples is the Tesla Classic 8 electric truck which can go 500 miles on a single charge. Using IoT, the vehicle can call 911 if the driver isn’t responding. IoT can tap into large fleets that can give them information on routes, fuel consumption, performance data, and traffic. Integrated cloud-based platforms can gain multiple benefits, such as tracking vehicle positions to monitor time and efficiency.
Smart manufacturing
Smart infrastructure is powering Smart cities and revolutionizing the automotive industry. It will not take long for street signs and traffic signals to become a thing of the past. Our connected cars in the future will be smart enough to take twists and turns on busy roads with Smart technology. For this, we require a drastic change in how automotive manufacturers approach a Smart car. As a result, software and hardware development will need to be combined to create that perfect car, straight from the future.
Braking Point
The Independent points out that by 2030, the standard cars will have evolved from merely assisting drivers to fully taking control. IoT technology will power tomorrow’s car with sophisticated sensors and cameras and the ability to communicate with road signages and markings. Most payments will happen online, indicating that drivers will no longer have to carry cash. Consequently, vehicles pay their insurance themselves!
In conclusion, with the influence of IoT in automotive industry, millions of drivers can connect with over-the-air software to receive updates, information, and bug fixes. V2V, V2I, and V2X connectivity will launch a new era in fleet management. With IoT, a Wifi connection will be enough to make the drive smooth, safe, and 100% hassle-free. So, there’s no braking point but full throttle with max safety and much more than you might think.
Looking for more information?
Check out our white papers on technology that can help improve your transportation and logistics business –
Get more insights on how we make it easy for IoT solutions in any business like healthcare with our automated testing solutions.