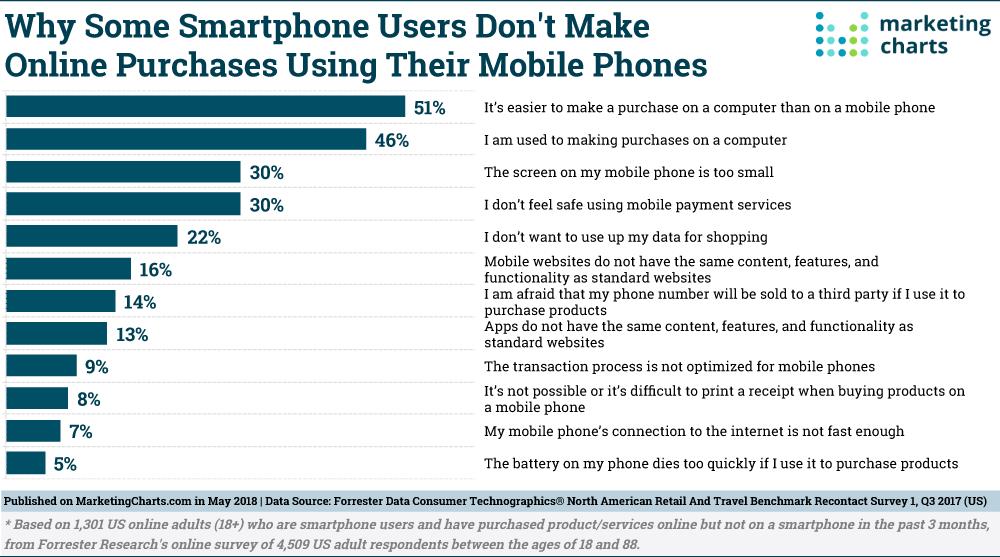
Introduction
The digital publishing industry has experienced significant growth in recent years, driven by advancements in technology and changing consumer preferences. As software engineers, we have witnessed firsthand the impact of these trends on the way content is created, distributed, and consumed. Discussed below are some of the key digital publishing trends and insights, drawing on various sources to provide a comprehensive overview of this rapidly evolving sector.
Digital Publishing Trends in 2024: An Overview of 8 Dynamic Industry Shifts
1. The Rise of E-books and Audiobooks
One of the most notable digital publishing trends is the increasing popularity of e-books and audiobooks. According to a report by Statista, global e-book revenue is projected to reach $15.6 billion by 2025, up from $12.8 billion in 2020. Similarly, the audiobook market has seen impressive growth, with the global market size expected to reach $15 billion by 2027, growing at a CAGR of 24.4% from 2020 to 2027.
This growth can be attributed to several factors, including the widespread adoption of smartphones and tablets, the convenience of digital formats, and the increasing demand for accessible and diverse content. As a result, publishers are investing more resources into digital formats, and authors are exploring new ways to reach their audiences through e-books and audiobooks.
2. Self-Publishing and the Democratization of Content Creation
The rise of self-publishing platforms like Amazon Kindle Direct Publishing (KDP), Smashwords, and Draft2Digital has made it easier than ever for authors to publish their work without the need for a traditional publishing house. According to a report by Bowker, the number of self-published titles in the United States grew by 40% in 2018, reaching over 1.6 million.
This democratization of content creation has led to an explosion of new voices and genres in the digital publishing space, providing readers with a wider range of choices and fostering a more diverse literary landscape. Additionally, self-publishing has allowed authors to retain more control over their work and earn higher royalties, making it an attractive option for both established and emerging writers.
3. The Emergence of Subscription Models and Digital Libraries
Another significant digital publishing trend is the rise of subscription models and digital libraries, which offer readers access to a vast collection of e-books and audiobooks for a fixed monthly fee. Platforms like Amazon Kindle Unlimited, Scribd, and Audible have gained popularity among readers, with Kindle Unlimited alone boasting over 3.4 million subscribers as of 2021.
These subscription services provide readers with an affordable and convenient way to access a wide range of content, while also offering publishers and authors a new revenue stream. As the popularity of these services continues to grow, we can expect to see more innovation in the subscription model space, with new platforms and features emerging to cater to the evolving needs of readers and publishers alike.
4. The Impact of Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning are playing an increasingly important role in the digital publishing industry, with applications ranging from content creation to marketing and distribution. For example, AI-powered tools like Grammarly and ProWritingAid are helping authors improve their writing by providing real-time feedback and suggestions, while machine learning algorithms are being used to analyze reader preferences and recommend personalized content.
In addition, AI and machine learning are being leveraged to automate various aspects of the publishing process, such as manuscript evaluation, metadata generation, and rights management. As these technologies continue to advance, we can expect to see even more innovative applications in the digital publishing space, driving greater efficiency and personalization for both creators and consumers.
AI is making waves in the publishing industry, transforming everything from content creation to personalized reader experiences. Imagine automated editing tools that refine manuscripts in minutes or AI-driven insights that help publishers predict the next bestseller. Leveraging AI in the Publishing Industry isn’t just about efficiency—it’s about unlocking new creative possibilities.
5. The Importance of Data-Driven Decision Making
As the digital publishing landscape becomes more competitive, publishers and authors are increasingly relying on data-driven decision-making to optimize their strategies and maximize their success. By analyzing data on reader behavior, preferences, and demographics, publishers can make more informed decisions about which titles to acquire, how to price their products, and how to target their marketing efforts.
Similarly, authors can use data to better understand their audience, identify trends and opportunities, and refine their writing to better resonate with readers. As the industry continues to evolve, the importance of data-driven decision-making will only grow, with those who effectively harness the power of data poised to thrive in the digital publishing ecosystem.
6. The Growing Role of Social Media and Influencer Marketing
Social media platforms have become increasingly important in the digital publishing landscape, providing authors and publishers with new avenues to connect with readers and promote their work. Platforms like Instagram, Twitter, and Facebook have given rise to a new generation of book influencers, who share their love of reading with their followers and help drive book sales through recommendations and reviews.
Influencer marketing has proven to be an effective strategy for promoting books, with a study by Tomoson finding that businesses earn $6.50 for every $1 spent on influencer marketing. As a result, publishers and authors are increasingly partnering with influencers to create buzz around their titles and reach new audiences. This trend is likely to continue as social media platforms evolve and new opportunities for engagement and promotion emerge.
7. The Expansion of Interactive and Multimedia Content
As technology continues to advance, digital publishing is becoming more interactive and immersive, with authors and publishers experimenting with new formats and multimedia elements to enhance the reading experience. Examples of this trend include interactive e-books with embedded videos, audio clips, and quizzes, as well as augmented reality (AR) and virtual reality (VR) experiences that transport readers into the worlds of their favorite books.
These innovations not only provide readers with a more engaging and immersive experience but also open up new revenue streams for authors and publishers. As the technology behind interactive and multimedia content continues to improve, we can expect to see even more creative and groundbreaking applications in the digital publishing space.
8. The Importance of Accessibility and Inclusivity
Digital publishing has the potential to make literature more accessible and inclusive, breaking down barriers for readers with disabilities and those from diverse backgrounds. E-books and audiobooks can be easily adapted to meet the needs of readers with visual impairments, dyslexia, or other learning disabilities, while the rise of self-publishing has enabled authors from underrepresented communities to share their stories and perspectives with a wider audience.
Publishers and authors are increasingly recognizing the importance of accessibility and inclusivity, with initiatives like the Accessible Books Consortium working to promote the creation and distribution of accessible digital content. As the industry continues to evolve, we can expect to see even greater emphasis on ensuring that digital publishing is accessible and inclusive for all readers.
Conclusion
The growth of digital publishing has been driven by a multitude of factors, from technological advancements to shifting consumer preferences and innovative business models. As we look ahead, we can expect to see continued growth in e-books and audiobooks, the further democratization of content creation through self-publishing, the expansion of subscription models and digital libraries, and the increasing influence of AI and machine learning on the publishing industry.
AI is transforming industries, automating processes, and driving smarter decision-making. Whether you’re looking to enhance efficiency or create intelligent solutions, Mindfire has you covered. Unlock innovation with Mindfire’s AI development services—smart solutions for a smarter future!
By staying abreast of these trends and insights, publishers, authors, and software engineers alike can better navigate the rapidly evolving digital publishing landscape and capitalize on the opportunities it presents.
Looking to enhance your digital publishing capabilities? Wondering where to find innovative digital publishing solutions tailored to your needs? Look no further than Mindfire Solutions! As a pioneer in the field, we deliver cutting-edge development services for the publishing industry, ensuring seamless content management and enriched user experiences.